Hi there 👋
How can I help you today?
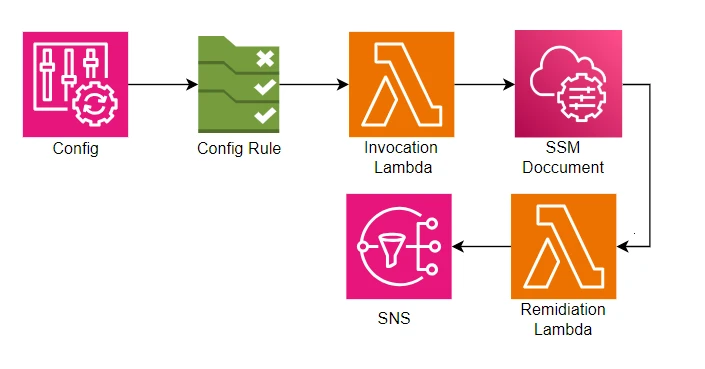
In the dynamic landscape of cloud computing, maintaining governance and compliance is paramount. AWS Config provides a robust solution for monitoring and managing AWS resources, and in this blog post, we'll explore a hands-on approach to automating AWS Config with a custom rule to enforce resource tagging. This streamlined workflow will leverage AWS Lambda, AWS Systems Manager (SSM) documents, and Amazon Simple Notification Service (SNS) to automate and enhance the compliance management process.
Resource tagging within AWS emerges as a robust mechanism, wielding significant capabilities to categorize and organize our diverse array of resources. Tags serve as a linchpin in this endeavor, offering a multifaceted solution that not only facilitates streamlined resource identification but also plays a pivotal role in cost allocation. Moreover, and perhaps most crucially, tags serve as a formidable instrument for enforcing stringent security and compliance policies within our AWS infrastructure.
In the context of this blog, our focal point centers on EC2 instances — the workhorses of our cloud environment. Through a comprehensive exploration, we will illuminate the process of automating the enforcement of mandatory tags on these instances. By implementing this automation, we not only streamline the organization and identification of our EC2 resources but also bolster our security and compliance postures.
The automation process will encompass the establishment of clear guidelines for required tags, ensuring that every EC2 instance is adorned with the necessary metadata. This not only enhances the clarity and efficiency of resource management but also aligns with industry best practices and regulatory standards, forming a resilient foundation for a secure and compliant AWS environment.
Creating a Custom AWS Config Rule:
Embarking on the journey to fortify our AWS resource compliance, we will harness the capabilities of AWS Config Rules to tailor custom criteria aligned with our organizational standards. Our initial focus will be on sculpting a bespoke AWS Config rule dedicated to meticulously assessing the compliance status of our AWS resources, with a keen emphasis on the intricacies of EC2 instances.
This custom AWS Config rule serves as a powerful tool, allowing us to define and enforce specific configurations, settings, and conditions that align with our compliance objectives. By centering our attention on EC2 instances, we aim to scrutinize and validate their configurations against our pre-established standards, ensuring that they adhere to the prescribed best practices and security requirements.
The creation of this custom rule empowers us to proactively monitor and evaluate the compliance posture of our EC2 instances, providing a proactive mechanism to identify and address any deviations from our defined standards promptly. This not only enhances the overall security and reliability of our AWS environment but also establishes a foundation for continuous compliance monitoring and enforcement across our cloud infrastructure.
import boto3
import botocore
def evaluate_compliance(config_item, rule_parameters):
required_tags = rule_parameters.get('RequiredTags', [])
if 'resourceType' in config_item and config_item['resourceType'] == 'AWS::EC2::Instance':
instance_tags = config_item.get('tags', {})
for tag in required_tags:
if tag not in instance_tags:
return {
'compliance_type': 'NON_COMPLIANT',
'annotation': f'Missing required tag: {tag}'
}
return {
'compliance_type': 'COMPLIANT',
'annotation': 'All required tags present'
}AWS Systems Manager allows for efficient management of AWS resources at scale. We'll create an SSM document that outlines the steps needed to remediate the non-compliant resources. This document might include actions like adding missing tags to EC2 instances. Once the SSM document is in place, our Lambda function will execute it to perform the remediation actions on the non-compliant resources. This step ensures that your AWS environment is automatically brought back into compliance.
{
"schemaVersion": "2.2",
"description": "Remediate non-compliant EC2 instances by invoking Lambda for tag enforcement",
"mainSteps": [
{
"action": "aws:runLambdaFunction",
"name": "invokeLambdaRemediation",
"inputs": {
"FunctionName": "auto-ec2-remediation",
"Payload": "{\"action\":\"remediateEC2Tags\"}"
}
}
]
}
When AWS Config identifies non-compliance, an automated remediation process is crucial. AWS Lambda, a serverless compute service, will be our tool of choice. We'll create a Lambda function that triggers when the AWS Config rule reports non-compliance. This Lambda function will initiate the remediation process by invoking AWS Systems Manager (SSM) documents.
import boto3
def remediate_non_compliance(event, context):
ec2 = boto3.client('ec2')
for result in event['detail']['newEvaluationResults']:
resource_id = result['evaluationResultIdentifier']['evaluationResultQualifier']['resourceId']
try:
ec2.create_tags(Resources=[resource_id],
Tags=[{'Key': 'Environment', 'Value': 'Production'},
{'Key': 'Owner', 'Value': 'Admin'}])
print(f"Remediated missing tags for resource: {resource_id}")
except Exception as e:
print(f"Error remediating resource {resource_id}: {e}")
# Test the function locally
if __name__ == '__main__':
test_event = {
'detail': {
'newEvaluationResults': [
{
'evaluationResultIdentifier': {
'evaluationResultQualifier': {
'resourceId': 'i-0123456789abcdef0'
}
}
}
]
}
}
remediate_non_compliance(test_event, None)
To maintain comprehensive communication with stakeholders, we have implemented the utilization of Amazon Simple Notification Service (SNS) as a robust mechanism for disseminating timely notifications regarding the remediation actions taken. This strategic step is designed to elevate transparency within the organizational framework, ensuring that pertinent teams are consistently apprised of the specific alterations implemented to rectify non-compliant resources. By leveraging SNS, we aim to foster a heightened awareness among stakeholders, thereby facilitating a more informed and collaborative approach towards ensuring and sustaining compliance across all relevant facets of our operations.
import boto3
def send_sns_notification(message):
# Replace 'YourSNSArn' with your actual SNS Topic ARN
sns = boto3.client('sns')
sns_topic_arn = 'YourSNSArn'
try:
# Publish the message to the SNS topic
sns.publish(
TopicArn=sns_topic_arn,
Message=message,
Subject='EC2 Tag Remediation Notification'
)
print(f"SNS notification sent: {message}")
except Exception as e:
print(f"Error sending SNS notification: {e}")
By combining the capabilities of AWS Config, Lambda, AWS Systems Manager, and SNS, organizations can establish a robust and automated compliance management workflow. This not only reduces manual intervention but also enhances the overall security and governance of AWS resources..


